AddTrust External CA Root Expired 30 May 2020
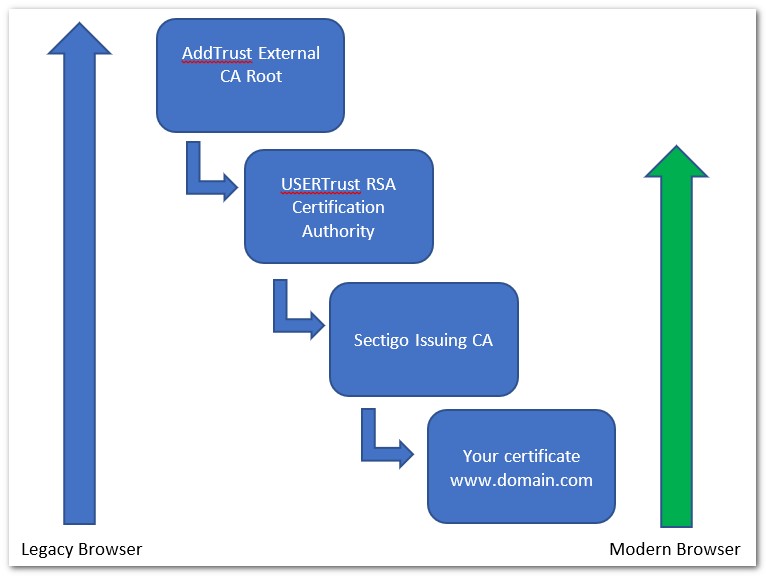
On 30 May 2020, AddTrust External CA Root root certificate expired.
Although Sectigo (formerly Comodo) claimed that the transition would not affect customers in any way, this led to the loss of functionality of some systems.
How to fix the situation?
It is not required to re-issue the certificate – just change the chain on the server.
If everything works for you normally, then no action is required!
Below are obsolete chains (left) and their replacements
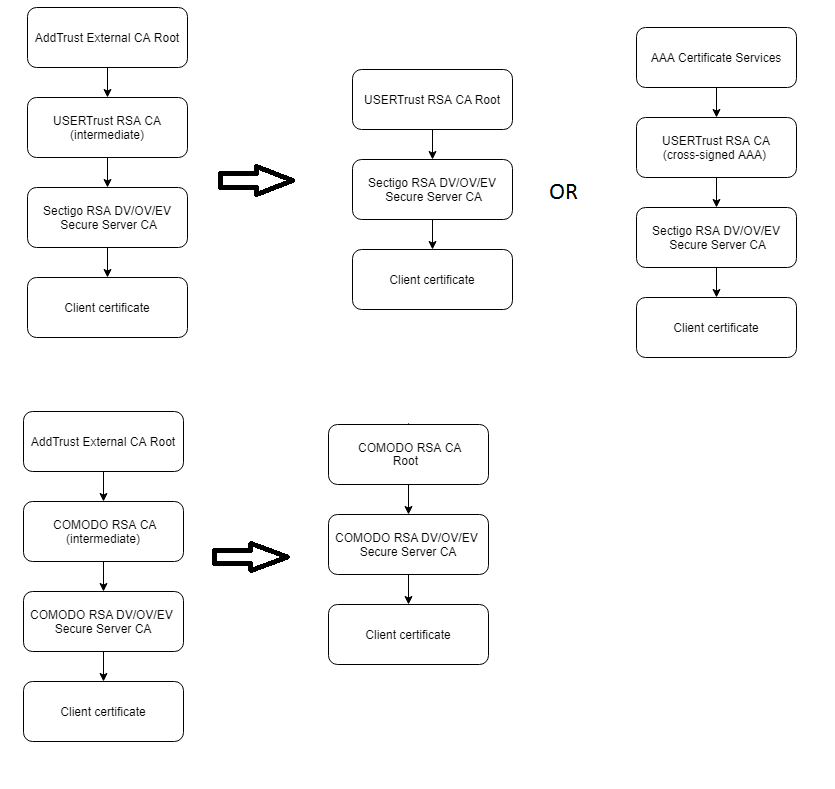
How to determine right chain? Open your certificate with a double click and find the “Issued By” field.
- If you see “Sectigo RSA Domain Validation Secure Server CA”, then files of the current chain can be downloaded here or ca-bundle (for NGINX, Apache)
- If you see "Sectigo RSA Organization Validation Secure Server CA", then files of the current chain can be downloaded here or ca-bundle (for NGINX, Apache)
- If you see "Sectigo RSA Extended Validation Secure Server CA", then files of the current chain can be downloaded here or ca-bundle (for NGINX, Apache)
- If you see “COMODO RSA Domain Validation Secure Server CA”, then files of the current chain can be downloaded here or ca-bundle (for NGINX, Apache)
- If you see “COMODO RSA Organization Validation Secure Server CA”, then files of the current chain can be downloaded here or ca-bundle (for NGINX, Apache)
- If you see “COMODO RSA Extended Validation Secure Server CA”, then files of the current chain can be downloaded here or ca-bundle (for NGINX, Apache)














